Often, people face challenges when deciding on which digital currency they should choose as some are centralized, which may take away from the benefits that they may be in search of in the virtual monies. Let’s take a look into the different types of blockchain available on the market, their features, advantages, and disadvantages:
Public
This type also goes by the name distributed, and it operates on a large network where execution takes place by means of digital assets which the users exchange over the platform. These types of systems are open to everyone as their source code is public information. It is thus possible for members of the community to make changes to it when they wish. A good example of such a network would be Bitcoin.
Decentralized
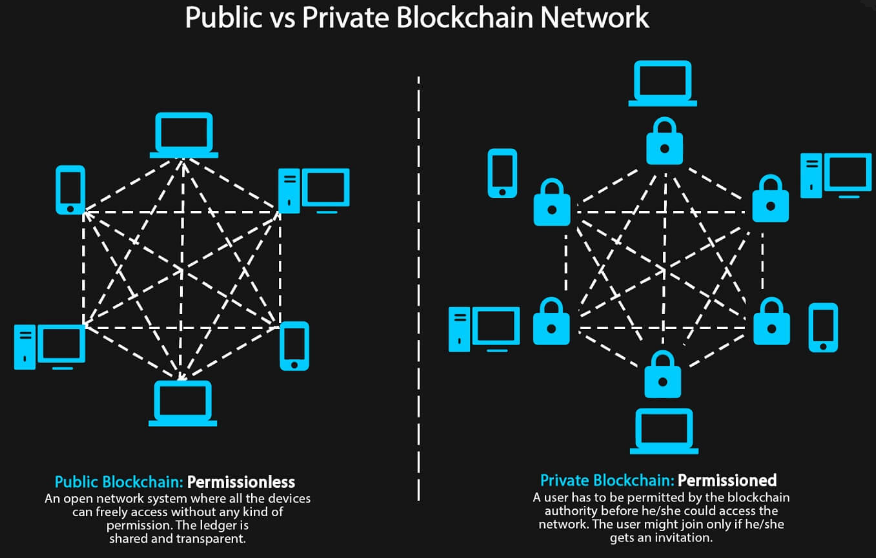
This type, also known as an authorized system, has control as to what the users can do while in the network. Exchanges can take place using digital assets or not. Also, the source code could be open or otherwise. An excellent example, in this case, would be RIPPLE. Where a system is decentralized, security is at a high level, and users can not only store but also exchange information at reduced costs, which makes such systems attractive.
Private
This system also goes by the name centralized. You will find that such networks tend to be much smaller than the two above, and in most cases, there are no tokens in play. Access to these systems is not open as the companies in place decide who can see the information. These systems come in handy to companies which would wish to keep their data private.
The difference between a centralized and a decentralized system has been a hot topic for a while as users of both systems have been quick to come to their defense. Take the internet as an example. It is a form of a decentralized network. However, the apps that you find in it are of a centralized nature such as social media spaces. You require the decentralized system to access these centralized apps. Many companies use different types of technology - find out which exactly.
If you look at it in this manner, you begin to see that the concept of centralization or otherwise is so big that covering it all could be impossible. Many firms that choose to use this technology want to control access as they wish to preserve their confidentiality and that of their clients. Let us look at a few more examples that could help you understand this concept better:
The Open Systems

Using Bitcoin in this example will make it easier for you to understand the workings of open source code systems as this digital currency has been around for a while. This system is available to anyone with a computer as you can download it at will and use it to look at transactions. What’s more, you could also provide the computing power needed to mine blocks, thus becoming a participant in the community.
This system has been around for a while, and thus people trust it and with many people using it, the security is at a high level, as compared to digital currencies that are new on the market. Where the number of computers in a network is small, it becomes easy for a hacker to infiltrate the system and make changes to the information on the platform, which cannot happen in the case of Bitcoin. However, with this added security, people have to adapt to a lengthy validation system which takes as much as ten minutes to complete, not to mention the high amount of energy required for the process.
Also, there is a limitation in the supply of the tokens as its creator wanted a certain amount of money in circulation at a time. Scarcity of the same is thus a possibility.
Ethereum is another digital currency which interested participants in the community can consider as it allows more applications to take place as compared to the former. This public network takes a few seconds to complete validation, and there is no limit as to the amount of money that can be in circulation at a given time. The language used in its architecture allows for smarts contracts to take place, which enables the creation of decentralized apps. However, it provides lower security as compared to its counterpart, which is a setback that could scare away potential investors.
Private Networks
Important

Many companies prefer to use these networks as they do not trust the transparency involved in public systems. For any firm with secrets or a need for anonymity, this is the way to go. There is an administrator in place who oversees the operations in the network, which serves as a disadvantage to the system. If a hacker gets into the administrator’s data, they can get access to other computers in the network, which serves as a security threat to users of the same.The choice of either of the systems will depend on the purpose of use, the need for anonymity as well as the importance of security. What option would you choose?




